Single sign-on (SSO)
Beyond the standard method of signing in with an email-password, we offer the option of using Enterprise Single Sign-On (SSO). This means your team can log in using the same credentials they already use for other applications and services within your organization and get authenticated using your company's Identity Provider (IdP).
Note
It's important to note that SSO is a premium feature and can be activated specifically for your organization upon request. To enable this feature, please speak with your Ocrolus Account Manager.
Important to know
- Compatible with major identity providers (IdP): We support the Security Assertion Markup Language (SAML) protocol for SSO. SAML allows our system to talk smoothly with various IdPs like PingOne, Google, Azure, Okta, Salesforce, etc.
- Supported SAML workflow: Currently, Ocrolus supports the Service Provider (SP) initiated SAML workflow. IdP initiated workflows are not supported.
- Multiple SSO connections: Your organization isn't limited to just one SSO setup. You can have up to five active SAML connections. This flexibility means you can accommodate different departments or teams that might use different identity providers.
- Option to disable email-password login: Once you have SSO set up and running, you can choose to turn off the standard email-password login method.
Configure SAML integration
This configuration option is accessible to only the org managers/admins. To configure the SAML integration, perform the following steps in Orcolus Dashboard:
-
Log in to the Ocrolus Dashboard.
-
Click on the Account & Settings icon located at the top right corner of your screen and select Login Methods from the dropdown list.
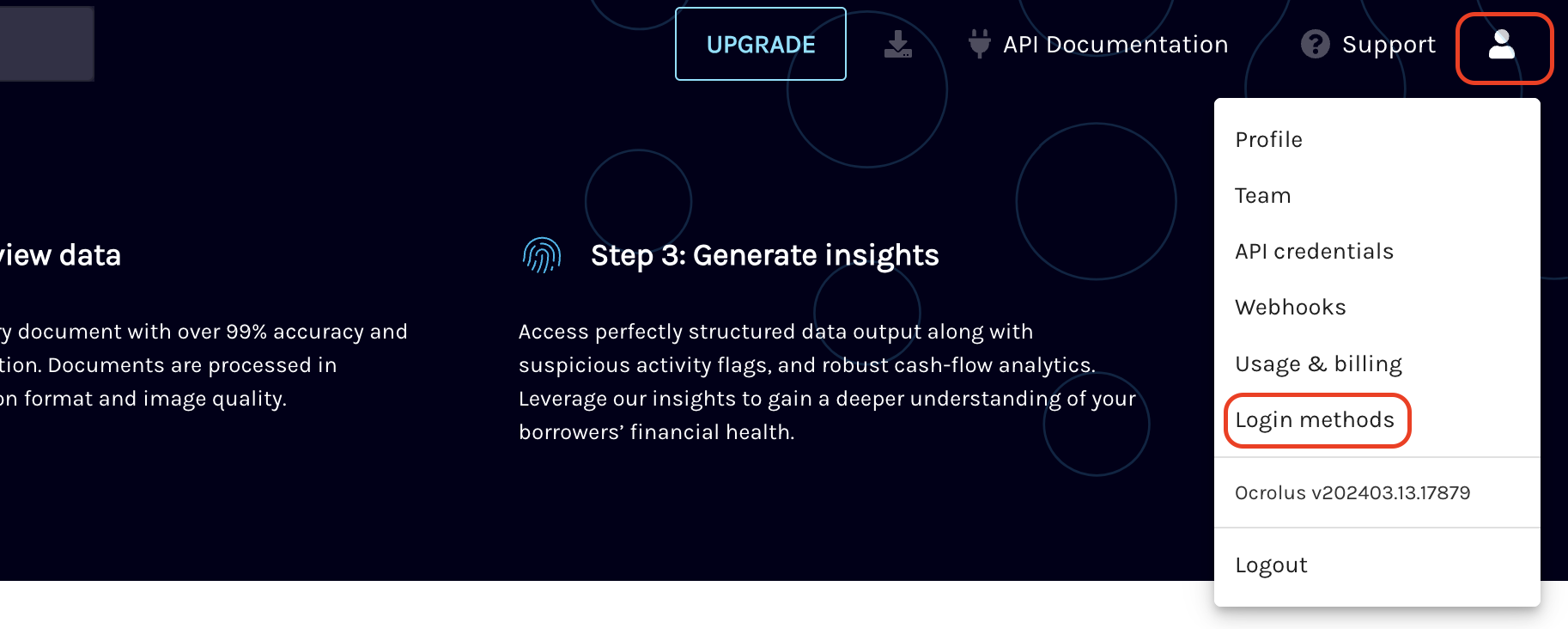
Note
If the Login Method option is not visible, either you are not logged using org manager account or the feature is not enabled for your organisation. Please contact Ocrolus customer support at [email protected] to enable the SSO feature for your organization.
-
On the SSO connections page, select ADD CONNECTION.
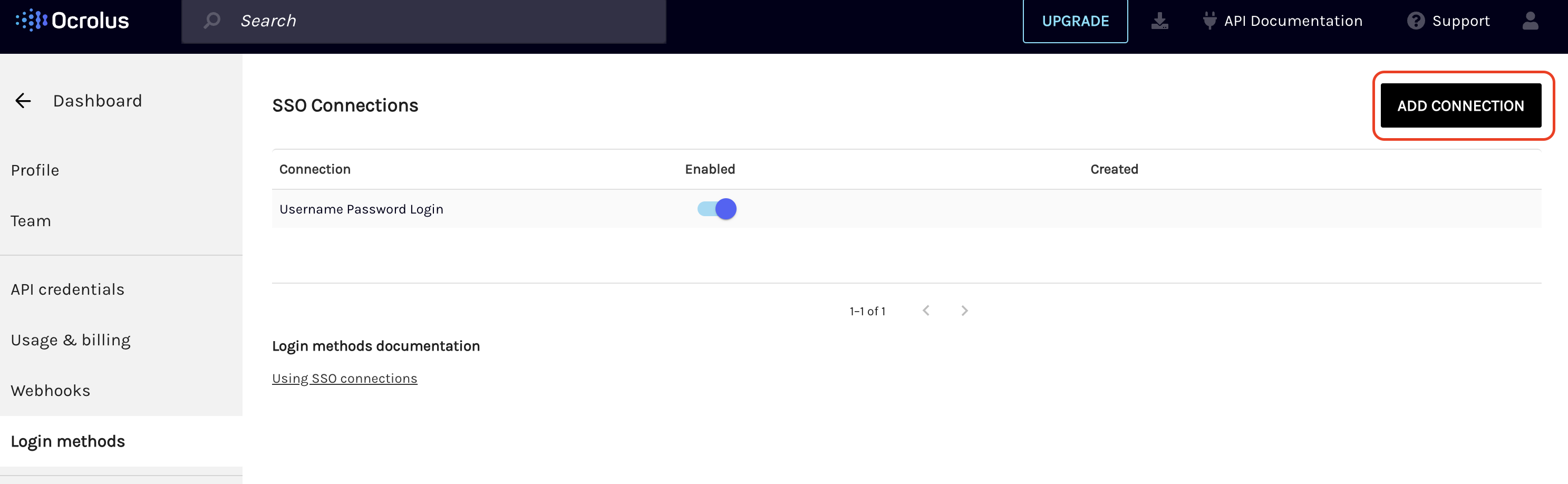
-
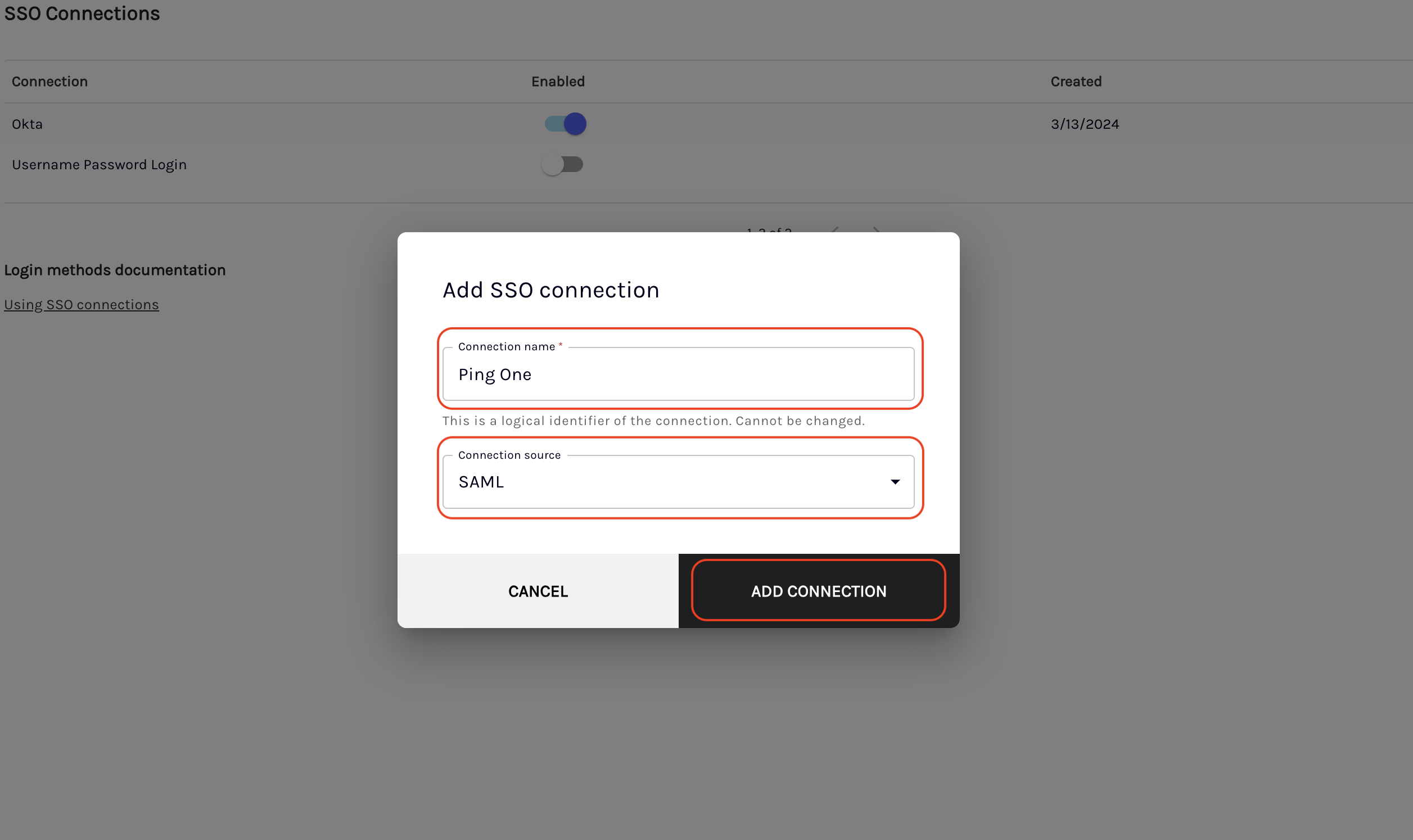
On the Add SSO connection pop-up, enter the following details and then click on ADD CONNECTION:
- Connection name: The unique identifier of the SAML connection within your organization. The connection name will be displayed upon login as "Login via ".
- Connection source: Ensure that the SAML is selected.
-
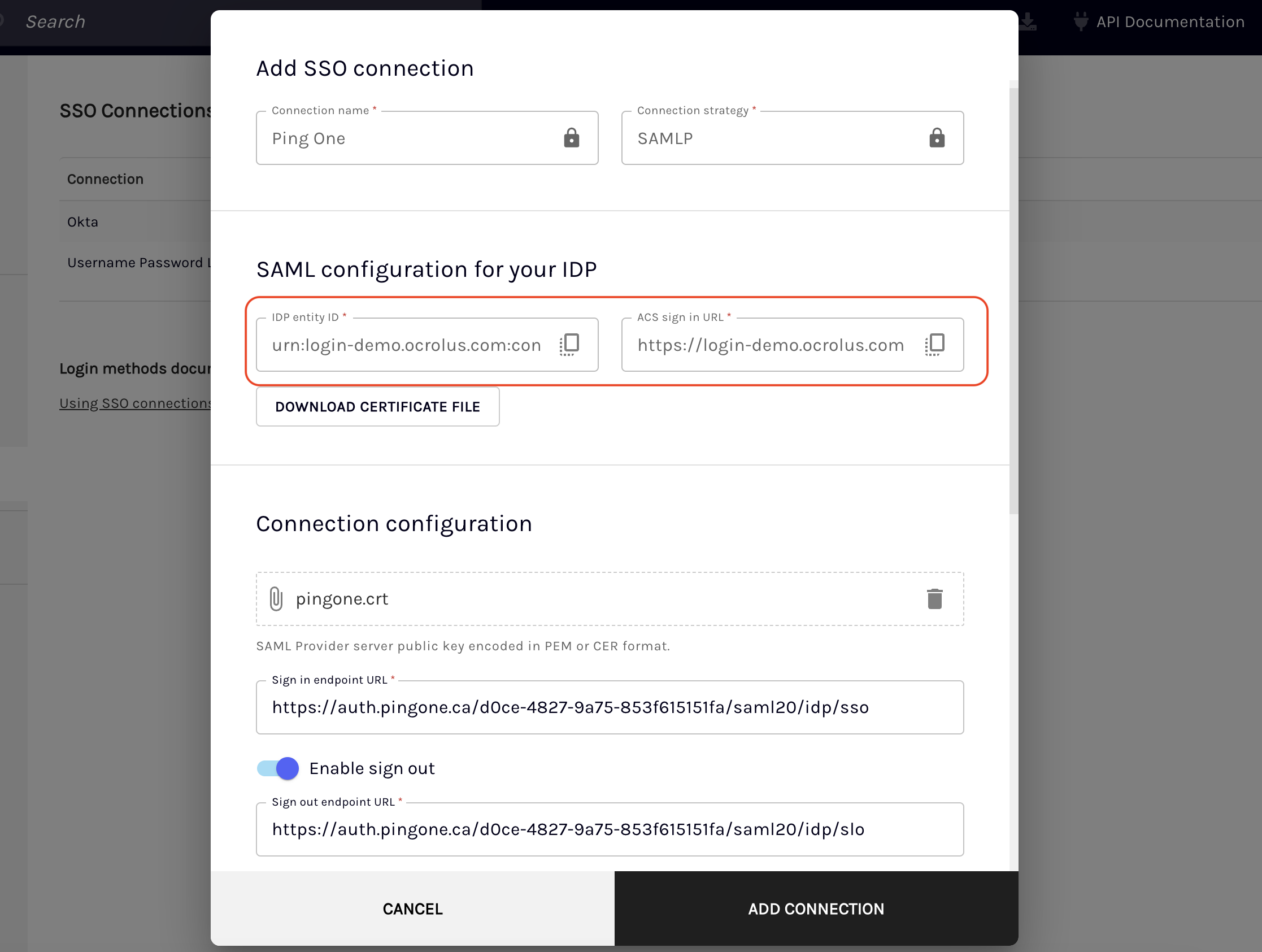
After submitting the connection name, Ocrolus will provide an Entity ID and an Assertion Consumer Service (ACS) URL. Enter the provided Entity ID and ACS URL in the respective fields to configure your IdP (PingOne, Google, Azure, Okta, Salesforce, etc.).
-
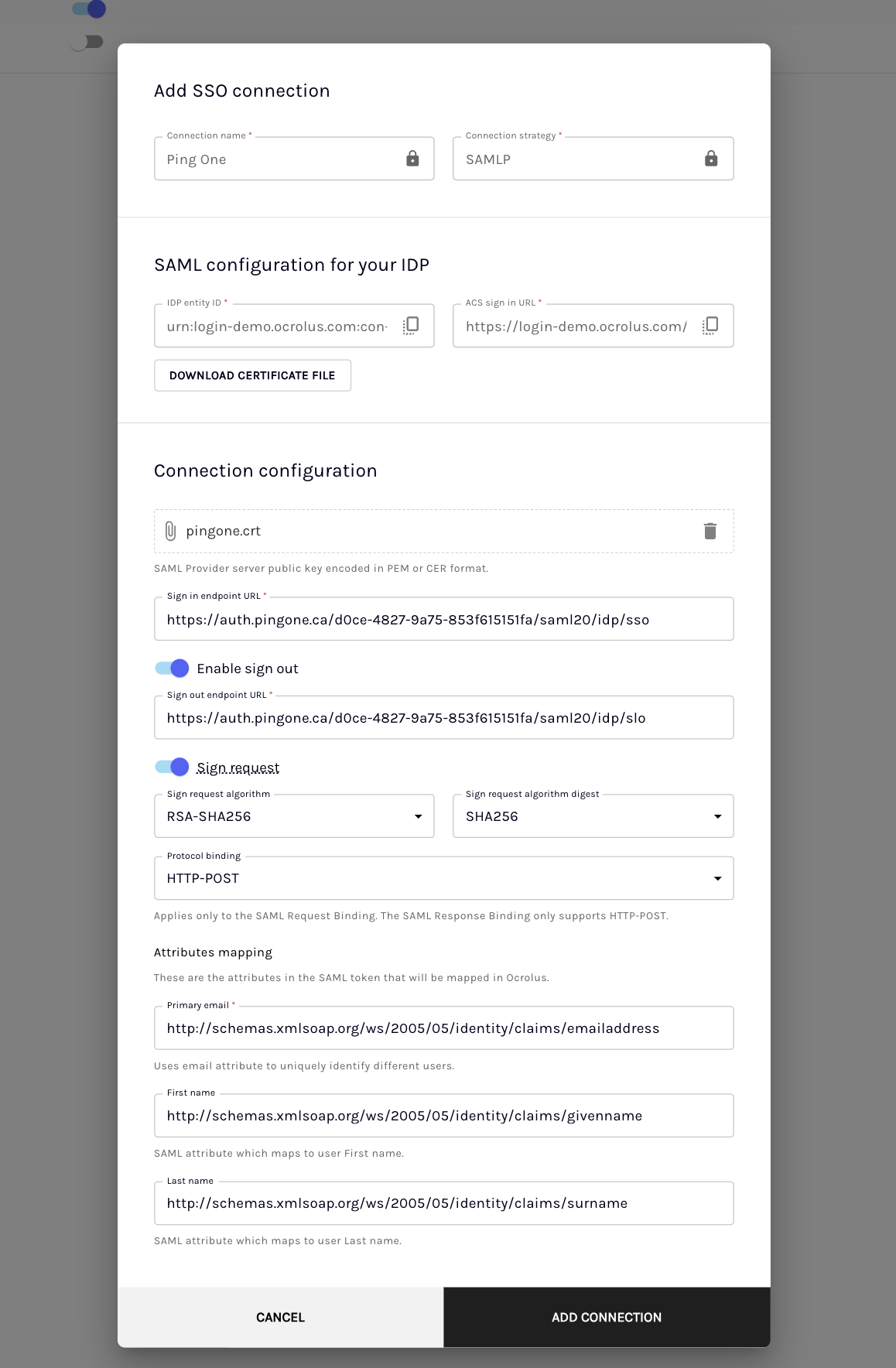
Under the Connection configuration section, enter the SAML configuration provided by your IdP on setting up SAML in the respective fields.
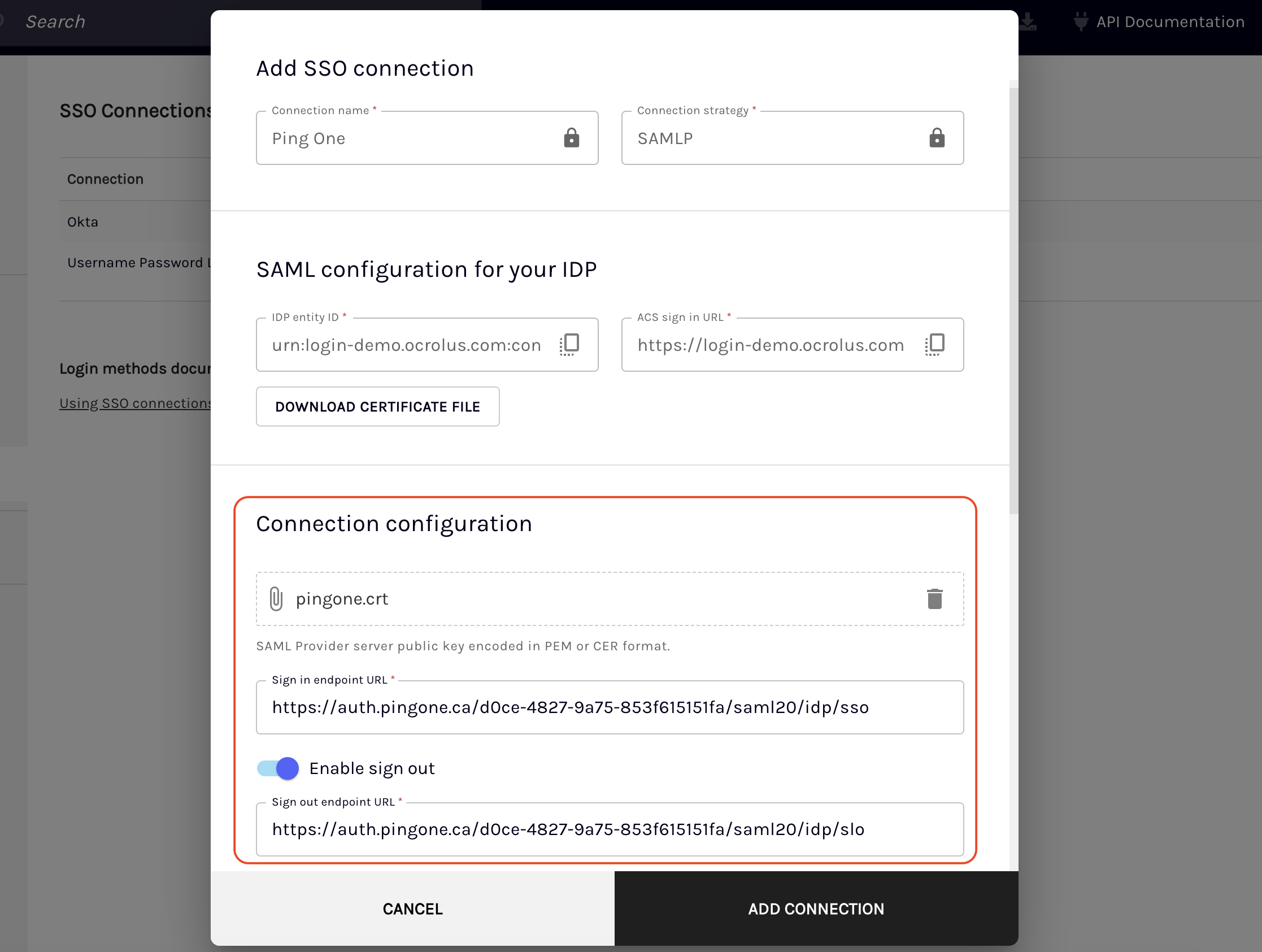
-
Save and enable the connection to test it out.
-
After successfully testing your new SSO configuration, you have the option to disable password-based login if needed. If you choose to do so, please ensure that you log out and then log back in via the SSO connection as you cannot disable the connection (password-based) you are currently logged in with.
SAML configuration attribute definitions
This section includes a list of attributes and their explanations that you will come across while setting up the SAML configuration:
| Fields | Descriptions |
|---|---|
| Sign In URL (Required) | This is the destination URL for sending SAML authentication requests, commonly referred to as the single sign-on (SSO) endpoint. |
| Signing Certificate (Required) | The public key from your IdP, that's used for verifying the signatures on SAML assertions. |
| Sign Out URL | This URL is used for sending SAML sign-out requests and is often termed the single logout (SLO) endpoint. |
| Sign Request | Activates the option for SAML authentication requests to be signed. |
| Sign Request Algorithm | The specific algorithm employed for signing SAML requests. |
| Sign Request Algorithm Digest | The digest algorithm is utilized in the signing process for SAML requests. |
| Protocol Binding | This defines the method of transmitting SAML requests. If SAML requests are unsuccessful, make sure to check the protocol binding setting on your IdP. The available protocol binding options are: |
| Attributes Mapping | User attributes defined in the SAML response that will be mapped to the corresponding fields: |
Note
While mapping the attribute, ensure that these user attributes are correctly defined and configured in your Identity Provider (IdP) for accurate mapping and user identification. If the Primary Email is not returned in the SAML response, you will receive an Access Denied error.
Updated over 1 year ago